Tech Offers
These are the new technologies that the COSMO team developed and they are available for licensing and commercialization. Please contact the respective Principal Investigator (PI) for further discussion.
Technology Overview
Cyber-Physical Systems (CPS) provide the foundation of our critical infrastructures, which form the basis of emerging and future smart services and improve our quality of life in many areas. In such CPS, sensor data is transmitted over the network to the controller, which will make real-time control decisions according to the received sensor data. Due to the existence of spoofing attacks (more specifically to CPS, false data injection attacks), one has to protect the authenticity and integrity of the transmitted data. However, the resource-constrained field devices like sensors cannot afford conventional signature computation. Thus, we introduce two Lightweight Signature schemes LiS, which are suitable for continuous message authentication commonly seen in cyber-physical systems.

Our LiS scheme has two versions, which are briefly illustrated as follows. (We refer the reader to our paper for more details). LiS1 is non-adaptively secure and suitable for small messages with a few hundred bits but is the most efficient one. The second protocol LiS2 can provide adaptive security, but one more cryptographic hash function is required.
I. Non-adaptively Secure Signature Scheme: LiS1
LiS1 relies on chameleon hash functions (CHF), Bloom filters (BF), and Universal Hash Functions (UHF). The LiS1 is briefly described as follows (see also in Figure 1).
Init: A signer A first runs the key generation algorithm of the chameleon hash function (skCH,pkCH) := CHF.KGen() to generate a pair of secret/public key, and samples a random key k for the universal hash function UHF, a random message M, and an initial random value r0'. A initializes Bloom filter instance BF with size l and false positive parameter ε. For i∈[l], A generates l dummy random values such that ri' := UHF(k,ri-1'), and the verify points ti := CHF(M,ri') for future use. Meanwhile, A inserts those verify points into the Bloom filter BF.insert(ti). A random variable r' := r1' which is used for generating the next signature. Eventually, the secret key and the verification key of A are skA := (skCH, k,r',M) and vkA := (BF, pkCH).
Sign: Upon obtaining a message m that requires authentication, the signer A first retrieves the stored secret key skA := ( skCH, k,r',M). A can compute the signature for m as x := CHF.Coll(skCH,r',M,m) = M* skCH + r’ – m* skCH. Then, A can send m together with the signature x to the verifier. After this, A updates the dummy randomness to the next one as r' := UHF(k,r').
Verify: Upon receiving a message m and its signature x from the signer A, the verifier B verifies it by checking that whether the resultant hash value t=CHF(m,x) is in the Bloom filter, i.e., BF.check(t).

Fig.
1. Overview of LiS. KGC stands for key generation center
II. Adaptively Secure Signature Scheme: LiS2
The second version LiS2 relies on the first version scheme and a hash function H. The LiS2 is briefly described as follows.
Init: This algorithm is identical to that of LiS1.
Sign: To authenticate a message m, A first samples a random value N, and computes y := H(m||N). Then the signer A generates the signature x for y as x := CHF.Coll(skCH,r',M,y) = M* skCH + r’ – y* skCH. Then, A can send m together with the signature x to the verifier. After this, A updates the dummy randomness to the next one as r' := UHF(k,r').
Verify: Upon receiving (m,N,x) from the signer A, the verifier B verifies it by checking that whether the resultant hash value t=CHF(H(m||N),x) is in the Bloom filter, i.e., BF.check(t).
 Fig.
2. Overview of Server-aided Replenishment (SAR)
Fig.
2. Overview of Server-aided Replenishment (SAR)
Technology Features / Specifications
LiS has the following features and advantages.
- LiS1 is strong existential unforgeable against non-adaptive chosen message attacks in the standard security model. LiS2 is strong existential unforgeable against adaptive chosen message attacks under the random oracle model. Both our DS schemes are proved without non-standard forking lemma comparing to prior Schnorr like online/offline digital signature schemes.
- Our DS schemes enable the outsourceable verification key replenishment, in such a way that the verification key can never run out. Our replenishment has no impact on signer over prior work.
- Due to the optimized instantiation of CHF, Our DS schemes can achieve multiple-times performance improvement over prior work.
Potential Applications
LiS1 and LiS2 can be widely used in cyber-physical systems. It enables resource-constrained signers to (continuously) authenticate messages. Below are a few examples of potential applications.
- Satellite Navigation Systems
- V2X Systems
- Maritime Systems
- Smart Grid
Benefits
The mentioned techniques provide efficient signature mechanism that can support the fast and continuous message authentication in CPS, while being easy to compute on the resource-constrained devices. Specifically, our signature schemes have a fast signing procedure and an optimal storage requirement on the signer side. The optimized signing algorithms are very efficient. Namely, our first scheme requires only three additions and two multiplications, and only one additional hash is needed in the second scheme to resist adaptive chosen message attacks. In addition, the size of the signing key in our schemes is a small constant-size bit string, which well fits CPS applications.
Please contact Prof. Zhou Jianying (SUTD) for further discussions on this technology.
Please download this technology offer LIS Lightweight Signature Schemes for Continuous Message Authentication.
Technology Overview
Traffic congestion is a key challenge in most cosmopolitan cities around the world, which leads to billions of dollars lost every year. With the economic growth, the congestion problem becomes much crucial in recent years for both developing and developed countries. Besides upgrading the costly infrastructure, a renovated traffic signal scheduling scheme is vital and more affordable to smooth the traffic movement in urban areas to alleviate the traffic congestion. In this solution, a macroscopic traffic network model is proposed to depict the traffic dynamics and a closed-loop traffic control strategy is designed based on the estimation of branching ratios at intersections. To reduce the computational complexity, a hybrid approach is proposed based on the congestion level identification and system partitioning method, which is based on machine learning algorithms.
Technology Features / Specifications
In this invention, a macroscopic model is proposed to depict the traffic dynamics involved in urban traffic systems. The link dynamics are described based on a novel cycle-based model and the link capacity, while the flow dynamics are proposed based on the discharge headways and saturation flow at intersections.

The large-scale traffic system is partitioned into several small subsystems, to reduce the computational complexity. The partitioning is based on the congestion levels identified by a learning-based strategy. After obtaining the system partition, various traffic light control schemes could be implemented in different subsystems with consideration of their individual traffic patterns. For example, for subsystems with low traffic demands, an optimized fixed-time strategy would be adopted with a low implementation cost. For subsystems with high traffic demands, optimization-based traffic responsive traffic light control schemes would be adopted, and the traffic light settings would be optimized in a real-time manner. Finally, the traffic light assignments will be coordinated to fulfil specific system-level performance requirements. The proposed closed loop, including networkwide congestion level prediction, traffic light scheduling and control, and traffic parameter estimation and prediction, can run autonomously to ensure high adaptivity and real-time responsiveness.

Potential Applications: A city-scale real-time traffic responsive traffic light control system
This proposed strategy has the following potential applications. (1) To upgrade an existing traffic light control system or enhance a new traffic light control system for better network performance, e.g., fewer traffic congestions, low travel delay time, higher network throughput. It relies on types of data that are commonly available nowadays via, e.g., cameras and/or V2X. (2) To help the traffic authorities handle emergencies efficiently, e.g., to quickly smooth traffic congestions due to traffic accidents via smart traffic light control, and to facilitate better public transportation system performance during peak hours. (3) The developed technologies on congestion region identification and turning ratio estimation may provide new means for traffic authorities to monitor real-time traffic conditions, analyse and predict network performance, and enhance route planning effectiveness for individual users, e.g., to make ETA more accurate than the current existing commercial solutions.
Benefits
The proposed technology will bring the following benefits: (1) to improve the traffic network performance and enhance real-time traffic responsiveness, e.g., reducing congestion and increasing throughput; (2) to quickly recover traffic flows from one-time events such as traffic accidents; (3) to ensure better performance of public transportation vehicles during peak hours via proper traffic light control, without significantly affecting other vehicles; (4) to facilitate real-time prediction of network performance. Our technology can be not only adopted in new traffic light control systems, but also used in existing control systems for functional upgrade with low retrofitting costs.
Please contact A/Prof. Su Rong (NTU) for further discussions on this technology.
Please download this technology offer A Hybrid Traffic Light Control Strategy with Congestion ID
Technology Overview
The fifth generation of mobile technology (5G) is designed to provide enhanced mobile broadband (eMBB), ultra-reliable low latency communications (URLLC) and massive machine type communications (mMTC). According to IMT-2020, 5G is supposed to perform ten to hundred times better in terms of peak data rate, latency and connection density. Due to the ubiquity of communication network, it also provides an added value on positioning services even in some GNSS-denied or constrained environments, e.g., indoors, urban canyon. The fundamental positioning techniques of cellular networks are classified as trilateration, triangulation, proximity, scene analysis and hybrid. Among which, time of arrival (TOA) based trilateration is one of the common methods utilized from 2G to 5G.
Positioning Reference Signal (PRS) is first defined in Long-Term Evolution (LTE) to perform TOA measurement as pilot signals. Another candidate of pilot signals in LTE for TOA measurement is the cell-specific reference signals (CRS). In 5G standards, the CRS is removed. Taking on the legacy of LTE, 5G utilizes Orthogonal Frequency Division Multiplexing (OFDM) waveform with flexible numerology. The first commercial 5G network was launched in 2019 based on the Release 15 specifications. Only since Release 16 forwards, 5G new radio (NR) downlink (DL) PRS was defined in 3rd generation partnership project (3GPP) Technical Specification (TS) 38.211 and TS 38.214. Until March 2020, corresponding positioning procedures and 5G NR DL PRS configurations were finalized in TS 37.355. These specifications pave the way for further verifying the performance of 5G PRS based positioning services. 5G NR PRS has flexible configurations and patterns, which are different from that of LTE CRS or other pilot signals adopted in OFDM system. There is a requirement of having proper timing recovery solution for 5G standard-compliant pilot signals, e.g., 5G NR PRS, thus, obtaining accurate timing estimate.
The proposed code-phase timing recovery solution is suitable for generalized pilot signal pattern including 5G NR DL PRS. It can be integrated with current 5G NR commercial network directly. The positioning process complies with that of 3GPP 5G standards. The proposed 5G carrier phase receiver provides more accurate carrier phase measurements and additional velocity estimate. The proposed 5G code phase receiver and 5G carrier phase receiver could potentially provide a more accurate localization service in 5G networks. The technology owner is interested in seeking technology licensing collaborator or manufacturing partner.
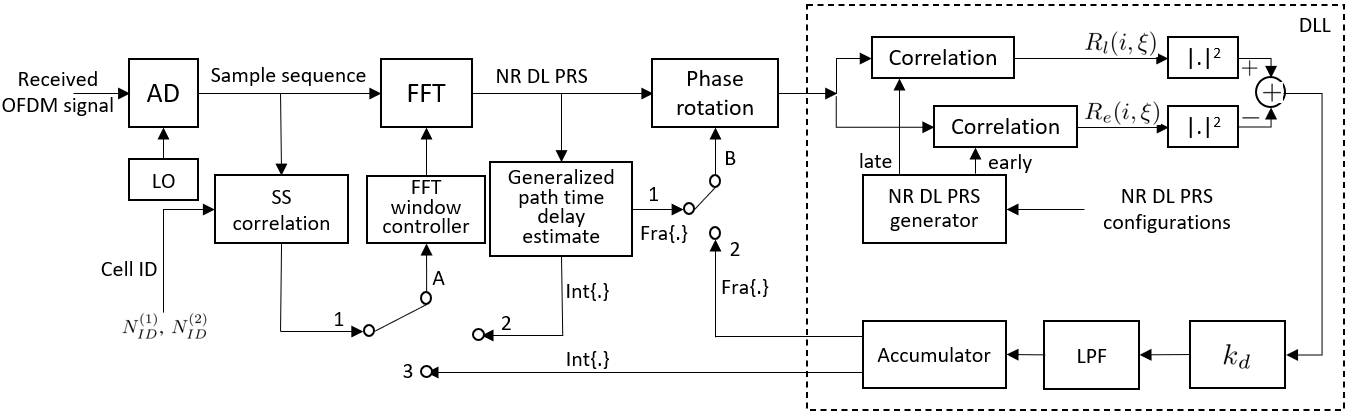
Block diagram of the proposed 5G NR DL PRS code phase-based receiver

5G Carrier Phase Receiver
Potential Applications
As shown in clause 4.3.1, 3GPP TS 38.305 (V16.0.0), the current 5G network supports downlink time difference of arrival (DL-TDOA) positioning method for localization services. 5G NR DL PRS is the potential reference signal adopted by 5G standards for measuring reference signal time difference (RSTD) in DL-TDOA. In addition, 5G NR DL PRS is defined in Release 16 (3GPP TS 38.214 (V16.1.0) and TS 37.355 (V16.0.0)). In the near future, the commercial 5G networks will support NR DL PRS based positioning method.
According to 3GPP TS 37.355 (V16.0.0), LTE Positioning Protocol (LPP) is used as point-to-point between a location server (E-SMLC, LMF or SLP) and a target device (UE or SET) to position the target device using position-related measurements obtained by one or more reference sources. Internal LPP positioning methods and associated signalling content include NR DL-TDOA. The timing recovery scheme described in this invention aims at implementing user equipment (UE) localization using the NR DL PRS signals in the actual 5G commercial network through NR DL-TDOA positioning method.
![LPP Configuration [TS 37.355] - Fig 3 LPP Configuration [TS 37.355] - Fig 3](/images/librariesprovider25/cosmo/5g-lpp-config-fig-3.jpg?sfvrsn=8fe454b2_0)
LPP Configuration [TS 37.355]
The figure above illustrates the positioning protocol in LTE and 5G NR networks. Our invention conforms to the 5G NR standards and positioning protocol in the following way:
- Once the localization service is initiated, the UE will NR DL PRS configuration of multiple base stations, i.e. NG-RAN, through assistance data defined in 3GPP TS 37.355 (V16.0.0) including but not limited to NR-DL-TDOA Assistance Data.
- With NR-DL-TDOA Assistance Data, UE obtains NR DL PRS reference signal configuration and pattern, together with other system information including frequency bandwidth, UE could receive and demodulate the expected NR DL PRS signals from expected gNodeB.
- After sampling the received NR DL PRS carried by CP-OFDM waveform, UE could apply the proposed three-stage code and carrier phase receiver to have an accurate estimate of timing error, the resulting time of arrival (TOA) will be obtained.
- Multiple gNodeBs result in multiple TOA at the UE, which can be used to calculate the NR DL TDOA on either UE or location server side. The measurements or location results could send back to location server.
It illustrates that the proposed code and carrier phase receiver can be integrated with the current 5G NR commercial network directly. The positioning process complies with that of 3GPP 5G standards. The proposed method could potentially provide a more accurate localization service.
Benefits
By applying this technology, the 5G-based positioning performance can be improved due to the introduction of phase-locked loop and corresponding carrier-phase based measurements, which play a similar role with that in GNSS positioning applications. The proposed method can be compatible with current 5G standards and commercial networks, which results in a more efficient and cost-effective positioning solution.
Please contact A/Prof. Tay Wee Peng (NTU) for further discussions on this technology.
Please download this technology offer 5G Positioning Using Code Phase and Carrier Phase Receiver
Technology Overview
Demands for fully integrated monolithic microwave integrated circuits (MMICs) have increased in the 5G/6G wireless communication systems market. In 5G/6G frequency division, higher working frequencies enabled highly miniaturized and fully integrated MMICs and the development of miniaturized on-chip passive components is indispensable. The miniaturized on-chip passive components with low port impedances can greatly reduce the size of MMICs by removing bulky impedance transformation circuits between the passive components and low impedance field-effect transistors (FETs). To realize highly miniaturized and low-impedance on-chip passive components, a microstrip-line structure with a short guided-wavelength and low characteristic impedance should be developed. Most of current structures have achieved a short guided-wavelength and low characteristic impedance but few efforts have been put on quality factor optimization. In this study, we proposed a novel microstrip-line structure employing big-small-holes periodically perforated ground metal (BSH-PPGM) that has a higher Q than the conventional structure and PPGM structure, and which will allow the development of high-Q and low impedance passive components on 5G/6G MMICs.

Top view of the microstrip line structure employing the proposed BSH-PPGM and simulation results
Potential Applications
This invention is applied to RF/MMIC designs especially to high frequency circuits in 6G applications where quality factor is extremely tough. It can be used in other processes where both metal density and quality factor performance are required and can also be used to tune the bandwidth of the circuit passband and stopband in 5G/6G applications. Firstly, this invention can improve passive devices quality factor by optimizing ground metal structure by 12% without adding additional manufacturing cost. Foundries with RF department such as TSMC, GF could be interested in using this invention to improve their passive device models. Secondly, this invention can be used in RF/mm-Wave circuits where passive devices are used. IC design companies such as Skyworks, Infineon Technologies, Qualcomm and so on could be interested in this invention for the application of their 5G/6G products, such as Sky5 suite (SKY5 A1007, SKY5 9600-11…), Infineon MMICs(BGT24LTR22N16, BGT24LTR22…).
Benefits
The quality factor of the proposed BSH-PPGM microstrip line is 12% large than traditional PPGM structure and is 5% superior comparing to small holes PPGM structure. As a result, RF/mm-Wave circuits performance will be increased by using this high Q BSH-PPGM microstrip line such as LNA, noise figure will be optimized. When it is applicated in RF/mm-Wave circuits such as frequency multiplier where wide bandwidth is required, it can also provide tunable solutions by changing the BSH density of the proposed invention.
Please contact A/Prof. Boon Chirn Chye (NTU) for further discussions on this technology.
Please download this technology offer A High Q Microstrip Line with Novel Big-Small-Holes
Technology Overview
This technology offer relates to a novel architecture design of a current-mode receiver that can be applied to sub-6GHz 5G and 6G communication systems.
In almost all situations and circumstances, communication signal received by a receiver is often accompanied by some blockers and interferers from both in-band or out-of-band frequencies, which may result in driving the receiver into saturation.
A traditional solution to address such effect is to utilize a current-mode direct conversion design, which avoids large voltage amplification at the LNA output. Another solution is to employ mixer-first receiver architecture. With LNA absent, it avoids any possible voltage amplification brought by the LNA. Although the current-mode and mixer-first architectures have certain tolerance for the blockers and interferers, they can still be saturated, especially with large blocker strength.
To alleviate this problem, a novel true-current-mode receiver architecture is invented. The receiver starts with a matching network. The matching network have two options, as shown in Figure 1.

Figure 1: Architectures of proposed current-mode receiver with different matching networks
Option-1 consists of three R-L-C parallel paths, and option-2 is a passive 90o hybrid coupler. Both create a virtual ground directly at the RF node, thus inducing voltage attenuation rather than voltage amplification at the RF node. This configuration improves the large-signal linearity greatly. Meanwhile, the noise of the matching resistor can be totally cancelled.
Technology Features & Specifications
The key technical specifications of three receivers are listed below.
(Matching Network Option-1) 4.0-dB NF / 17-dB Gain / 24-dBm IIP3 / 18-mW
(Matching Network Option-2) 4.8-dB NF / 23-dB Gain / 17-dBm IIP3 / 18-mW
Potential Applications
Firstly, this invention can be used in sub-6 GHz, 5G, and 6G receivers. With only one inductor or transformer utilized, it saves lots of chip area and cost.
Secondly, the invented receiver is suitable for SAW-less applications.
Thirdly, the invented receiver deals well with input signal with large signal strength. It shows a large dynamic range.
Benefits

Figure 2: Simulated P1dB of proposed receiver compared to that of the popular mixer-first receiver
There are two main benefits of the proposed true-current-mode receiver.
The first benefit is that they all show high linearity, which improves their tolerance to blockers significantly, making it to be suitable for highly dense wireless applications. The IIP3 is around 20 dBm. The simulated P1dB compared to that of the mixer-first receiver is provided in Figure 2. For out-of-band, the P1dB of proposed receiver is 7 dB larger than that of a typical mixer-first receiver.
Please contact A/Prof. Boon Chirn Chye (NTU) for further discussions on this technology.
Please download this technology offer Current-Mode Receiver Architectures With High Linearity
Technology Overview
In a V2X network, agents (including vehicles and pedestrians) are highly dynamic and safety consideration is always of the highest priority. We developed a new privacy framework to deal specifically with V2X networks, leveraging on the C-V2X and DSRC infrastructure. We bring inference privacy mechanisms to ITS networks. Inference privacy refers to the prevention of a service provider from performing statistical inference it has not been authorized to do. Our privacy-preserving framework can be efficiently implemented in vehicle OBUs, RSUs and gNodeBs to achieve monitoring and service provisioning while ensuring inference and data privacy with low computational overhead.
Our framework can be used to sanitize different kinds of C-V2X data such as basic safety message (BSM), images, video clips, etc. in order to suppress the embedded private information while maintaining the information necessary for the service provider to perform authorized tasks.

Technology Features/ Specifications
The technology consists of a pending patent and software algorithms. The patent is related to a framework for sanitizing various privacy sensitive C-V2X data.
Our privacy-preserving framework is a lightweight deep learning model which takes raw data such as BSMs and images as the inputs and outputs sanitized data with private information in the raw data maximally suppressed while the utility information is minimally distorted. Hence, the users of our technology can submit the privacy-preserved data instead of the raw data to the service provider.
Our framework can be trained offline and implemented in real-time on either portable devices or an edge server.
To deploy our framework, no modification is required in the current V2X communication systems because the size and the shape of the sanitized data are the same as those of the raw data.
Potential Applications
Insurance companies may assess a driver’s risk by collecting and analyzing his/her driving data via basic safety messages (BSMs) to determine the premium to be charged for the personal auto insurance. From the BSMs, insurers can recognize their customers’ driving patterns, e.g., normal or aggressive. Meanwhile, they are also able to infer other information from BSMs such as the locations their customers have been to. In our solution, we sanitize BSMs to obfuscate location information while maintain quality of utility services, e.g., recognition of {normal, aggressive, drowsy} driving.
In an autonomous people mover, the actions of the passengers are monitored by in-vehicle cameras. When passengers are performing aggressive, dangerous or suspicious actions, an alert should be raised. However, during normal operations, passengers’ personal identities are sensitive and private information. As a proof-of-concept, consider the following setup: We sanitize images/video clips captured by in-vehicle camera such that distraction actions such as talking on the phone, texting on the phone, etc., can be correctly recognized while the driver's sensitive information, e.g., gender, race, are maximally removed.
Benefits
The technology restricts the utility of C-V2X data to a service provider’s authorized mode of usage while minimizing the risk that the data can be repurposed for other uses, including the tracking of a vehicle.
Please contact A/Prof. Tay Wee Peng (NTU) for further discussions on this technology.
Please download this technology offer Privacy-Aware Service Provisioning In V2X Networks
Technology Overview
Ring voltage-controlled oscillator (VCO) based PLLs have several advantages over LC-VCO based PLLs, like smaller chip area, wider frequency tuning range and multi-phase output signals. However, the inferior jitter/phase noise of ring VCOs has always been the bottleneck of the overall PLL jitter/phase noise performance. To suppress ring VCO’s phase noise, feedforward phase noise cancellation (FFPNC) techniques and feedback phase noise cancellation (FBPNC) technique are widely researched. Most FFPNC and FBPNC based structures require numerous additional blocks, which consumes significant extra area and power. In order to suppress phase noise of the ring VCO with minimal area and power consumption, this technology offers a dual-path ring VCO based sub-sampling PLL (SSPLL) with a FBPNC technique.
Technology Features/ Specifications
The main structure of this design is based on the conventional SSPLL, which intrinsically eliminates divider noise and reduces the phase detector (PD)/charge pump (CP) noise by the multiplication of N2. Therefore, the PLL phase noise is mainly decided by the reference and ring VCO. The architecture of the proposed dual-path SSPLL is shown in Figure 1, which includes a sub-sampling loop and a frequency-locked loop. Compared to the conventional SSPLL, the main difference is the dual-path structure from the output of the SSPD to the low-pass filter (LPF). One path from the SSPD to the LPF is through sub-sampling charge pump 1 (SSCP1), the other path is composed of the high-pass filter (HPF) and SSCP2. The SSPD samples the ring VCO’s output and then hen the sampled output voltage is converted to an output current by the SSCP1 in path I. In path II, the sampled output is firstly high-pass filtered. Next, the filtered signal is also converted to a current signal and flows into the LPF. These two paths are operating simultaneously to control the LPF. Through properly setting the HPF’s high-pass frequency corner and SSCPs’ transconductances, a new in-band zero and pole are generated to enlarge the PLL bandwidth. Moreover, since the frequency of the introduced zero is smaller than the pole, the phase margin (PM) of the PLL is compensated. Consequently, the phase noise of the ring VCO contributed to the PLL is suppressed while the loop stability is still ensured.

Figure 1. Architectures of the proposed dual-path sub-sampling PLL
The prototype chip with the proposed technology is fabricated in a standard 28nm CMOS technology. The left part of Figure 2 shows the measured phase noise of the proposed SSPLL when gm,SSCP2 = 1.2gm,SSCP1. Compared to the conventional SSPLL, the phase noise is suppressed from 300kHz to 3.7MHz. The maximum phase noise suppression is [email protected] and the jitter integrated from 1kHz to 100MHz is improved from 3.52ps to 2.63ps. The closed-loop bandwidth is enlarged to around 6MHz. The right part of Figure 2 shows the measured results when gm,SSCP2 is set as 1.5gm,SSCP1 by changing the current mirror ratio (the simulated PM is degraded from 60° to 57°). The phase noise is suppressed from 200kHz to 4.1MHz compared to the conventional SSPLL. The maximum phase noise reduction is [email protected] and the integrated jitter is improved from 3.52ps to 2.66ps. The closed-loop bandwidth is enlarged to around 7.2MHz.
This technology does not require any additional delay line, clock generation or calibration circuits for the phase noise cancellation path. Furthermore, the cancellation path effectively improves the phase noise performance of the PLL and only consumes 160µW power.

Figure 2. Measure phase noise of the proposed SSPLL compared to the conventional one
Potential Applications
Firstly, this technology is suitable to provide local oscillator signals for low-power and small-area sub-6 GHz wireless transceivers.
Secondly, this technology is suitable to provide clock signals for low-power system-on-chips (SoCs) applications.
Thirdly, this technology is also suitable for low-power wireline communication systems.
Benefits
1) The existing PNC techniques always require additional voltage-controlled delay line, clock generation or calibration circuits. For the invented FBPNC technique, the implementation is much simpler, which only requires an additional HPF and SSCP. As a result, it largely simplifies the design process and scales down the die area.
2) Compared to several mW power consumption for the existing FBPNC techniques (e.g. 4mW for the FBPNC technique in [1]), the power consumption for the invented FBPNC technique only comes from the SSCP2, which is 160 µW. The power consumption can be drastically reduced to 4% of the existing FBPNC.
3) The VCO phase noise is effectively suppressed by the invented FBPNC technique while the loop stability is also ensured due to the phase margin compensation effect. For example, in the proposed SSPLL design, the phase noise could be improved by [email protected] while the phase margin is not decreased and kept at 60°.
Please contact A/Prof. Boon Chirn Chye (NTU) for further discussions on this technology.
Please download this technology offer Dual-path Sub-Sampling PLL with Feedback Phase Noise Cancellation Technique
Technology Overview
Conventionally, V2X use cases are developed with the SDK provided by hardware vendors, as a result, V2X use cases are deeply coupled with the hardware modules. At the same time, conventional approaches put all use case logics in a big executable, the big executable also served as the resource manager for the use cases, which make the approach hard to scale up and down.
This technology offer is an Intelligent Transportation System (ITS) Runtime Middleware that tackles the above mentioned two drawbacks of conventional approaches with two plugin engines. With this middleware,• system can be easily scaled up and down by incorporating independent use cases as plugins
• hardware from different vendors or even with different technologies can be supported automatically as plugins
• communication-standard stacks are facilitated in the middleware

Technology Features/ Specifications
This ITS Runtime Middleware has the following major functional blocks:
- Application plugin engine that loads and unloads V2X applications
- Event bus that facilitates a flexible pub/sub based message broker to enable communications among applications and runtime
- Message Queue that enables a producer/consumer pattern between applications and lower layer blocks
- Communication stacks implemented for SAE J2735, IEEE 1609.3 and IEEE 1609.4
- Radio plugin engine that interfaces with different V2X hardware modules, by default it comes with two working hardware modules plugins
- plugin for Quectel AG15 Module based on Qualcomm 9150 C-V2X ASIC
- plugin for Cohda Wireless MK5 Module based on NXP DSRC ASIC
Potential Applications
- V2X On Board Unit (OBU)
- V2X Road Side Unit (RSU)
- V2X Subsystem for Carputer OS
Benefits
- V2X application development and deployment are decoupled from specific V2X hardware
- V2X application suites can be easily scaled up and down for a V2X box
- V2X applications support both DSRC and C-V2X technologies automatically
- Standard compliance is facilitated by the middleware
- Extensions for new hardware support will be provided by the middleware
Please contact Prof. Guan Yong Liang (NTU) for further discussions on this technology.
Please download this technology offer ITS Runtime Middleware
